Saturday, 16 February 2013
Thursday, 14 February 2013
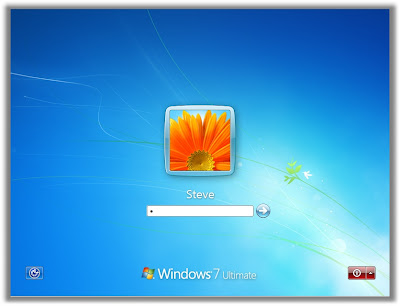
How to change the logon screen in windows 7
How to change the logon screen in windows 7
3. You will need to copy this image to
4. Now open the Registry Editor (Start -> Run -> Type regedit) and navigate to the following key
5. Double-click on OEMBackground and set the Value Data to 1.
6. Now log-off to see the new logon screen background. If you would like to revert back to the default background, just set the Value Data back to 0.
1. The image you need to set as the background should be a ".jpg" file and it’s size should not exceed "245KB".
2. The image resolution can be anything of your choice. However 1440 x 900 or 1024 x 768 is preferable.After compressing and setting the resolution for your image, save it as backgroundDefault.jpg.
"C:\Windows\system32\oobe\info\backgrounds"
You will need to create that path if it does not already exist on your computer.4. Now open the Registry Editor (Start -> Run -> Type regedit) and navigate to the following key
"HKLM\Software\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background"
If "Background" does not exist rightclick "LogonUI", select New and then Key, and then name it Background. Now locate OEMBackground (listed on the right side). If it does not exist, right-click Background and select New and then DWORD and name it OEMBackground.
6. Now log-off to see the new logon screen background. If you would like to revert back to the default background, just set the Value Data back to 0.
Tuesday, 12 February 2013
Aircrack-ng
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that
can recover keys once enough data packets have been captured. It
implements the standard FMS attack along with some optimizations like
KoreK attacks, as well as the all-new PTW attack, thus making the attack
much faster compared to other WEP cracking tools.
In fact, Aircrack-ng is a set of tools for auditing wireless networks.
In fact, Aircrack-ng is a set of tools for auditing wireless networks.
Saturday, 9 February 2013
Resource Hacker
Resource Hacker is a freeware
utility to view, modify, rename, add, delete and extract resources in
32bit & 64bit Windows executables and resource files (*.res). It
incorporates an internal resource script compiler and decompiler and
works on all (Win95 - Win7) Windows operating systems.
Viewing Resources: Cursor, Icon, Bitmap, GIF, AVI, and JPG resource images can be viewed. WAV and MIDI audio resources can be played. Menus, Dialogs, MessageTables, StringTables, Accelerators, Delphi Forms, and VersionInfo resources can be viewed as decompiled resource scripts. Menus and Dialogs can also be viewed as they would appear in a running application.
Viewing Resources: Cursor, Icon, Bitmap, GIF, AVI, and JPG resource images can be viewed. WAV and MIDI audio resources can be played. Menus, Dialogs, MessageTables, StringTables, Accelerators, Delphi Forms, and VersionInfo resources can be viewed as decompiled resource scripts. Menus and Dialogs can also be viewed as they would appear in a running application.
Friday, 8 February 2013
WIRESHARK
WIRESHARK
Wireshark is a network packet analyzer. A network packet analyzer will try to capture network packets and tries to display that packet data as detailed as possible.
You could think of a network packet analyzer as a measuring device used to examine what's going on inside a network cable, just like a voltmeter is used by an electrician to examine what's going on inside an electric cable (but at a higher level, of course).
In the past, such tools were either very expensive, proprietary, or both. However, with the advent of Wireshark, all that has changed.
Wireshark is perhaps one of the best open source packet analyzers available today.
batch file trick to screw up any pc
Wednesday, 6 February 2013
YUMI (Your Universal Multiboot Installer)
YUMI (Your Universal Multiboot Installer), is the successor to
MultibootISOs. It can be used to create a Multiboot USB Flash Drive
containing multiple operating systems, antivirus utilities, disc
cloning, diagnostic tools, and more. Contrary to MultiBootISO's which
used grub to boot ISO files directly from USB, YUMI uses syslinux to
boot extracted distributions stored on the USB device, and reverts to
using grub to Boot Multiple ISO files from USB, if necessary.
Aside from a few distributions, all files are stored within the Multiboot folder, making for a nicely organized Multiboot Drive that can still be used for other storage purposes.
Aside from a few distributions, all files are stored within the Multiboot folder, making for a nicely organized Multiboot Drive that can still be used for other storage purposes.
Monday, 4 February 2013
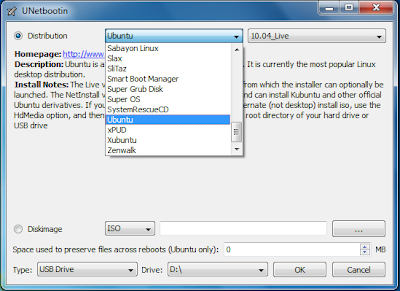
UNetbootin [linux boot]
UNetbootin allows you to create bootable Live USB drives for Ubuntu, Fedora, and other Linux distributions without burning a CD. It runs on Windows, Linux, and Mac OS X. You can either let UNetbootin download one of the manydistributions supported out-of-the-box for you, or supply your own Linux .iso file if you've already downloaded one or your preferred distribution isn't on the list.
Sunday, 3 February 2013
Trout 2.00
Trout is a simple visual traceroute and Whois
program. Pinging can be set at a controllable rate as can the frequency
of repeatedly scanning the selected host.
The built-in simple Whois lookup can be used to identify hosts discovered along the route to the destination computer. Features like parallel pinging and hostname lookup techniques will probably make this traceroute software the fastest currently available.
It can be considered as the best as it is free does its work quite impressively.
The built-in simple Whois lookup can be used to identify hosts discovered along the route to the destination computer. Features like parallel pinging and hostname lookup techniques will probably make this traceroute software the fastest currently available.
It can be considered as the best as it is free does its work quite impressively.
Ardamax Keylogger [with serial key]
Ardamax Keylogger is a keystroke recorder that captures user's
activity and saves it to an encrypted log file. The log file can be
viewed with the powerful Log Viewer. Use this tool to find out what is
happening on your computer while you are away, maintain a backup of your
typed data automatically or use it to monitor your kids. Also you can
use it as a monitoring device for detecting unauthorised access. Logs
can be automatically sent to your e-mail address, access to the
keylogger is password protected. Besides, Ardamax Keylogger logs
information about the Internet addresses the user has visited.
This invisible spy application is designed for 2000, XP, 2003, Vista, 7 and Windows 8.
This invisible spy application is designed for 2000, XP, 2003, Vista, 7 and Windows 8.
Beast (trojan horse)
Beast is a Windows-based backdoor trojan horse, more commonly known in the underground hacking community as a Remote Administration Tool or RAT. It is capable of infecting versions of Windows from 95 to XP. Written in Delphi and released first by its author Tataye in 2002, it became quite popular due to its unique features. It used the typical client–server model where the client would be under operation by the attacker and the server is what would infect the victim. Beast was one of the first trojans to feature a reverse connection
to its victims, and once established it gave the attacker complete
control over the infected computer. It mainly targeted three infection
sites:
Subscribe to:
Comments (Atom)